ESTABLISH AIRTIGHT SECURITY, COMPLIANCE, AND RESILIENCE AGAINST CYBER ATTACKS
Security alone is not enough anymore, you also need to be cyber resilient and compliant to align yourself with the dynamic nature of cyber threats. HybridValley will ensure you always stay one step ahead.
CYBER SECURITY IS EVOLVING AND WE WILL MAKE IT YOUR COMPETITIVE ADVANTAGE
Keep up with the dynamics of the cyber threat landscape and evolve with it. We will keep you ahead of your competition and drive security measures that inspire confidence.

Understand Your Past, Current, and Future Cyber Threats

Combine The Three Pillars Of Cyber Security (Strategic, Operational, and Tactical)

Deploy Custom Tailored Cyber Threat Security Solutions

Turn Your Cyber Threat Information Into Cyber Threat Intelligence

Solutions That Detect, Prioritize Any Cyber Risks You Face

Cyber Resilience That Not Only Mitigates And Absorbs But Also Repels
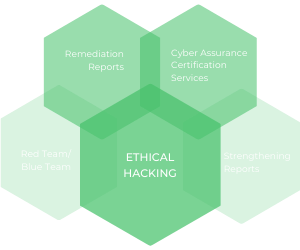
Penetration Testing
We offer thorough penetration testing services designed around identifying and remediating potential system vulnerabilities. We simulate a real attack scenario by employing ethical hacking and red team/blue team exercises to get an outsider’s perspective of your security and overall compliance.
Penetration Testing
We offer thorough penetration testing services designed around identifying and remediating potential system vulnerabilities. We simulate a real attack scenario by employing ethical hacking and red team/blue team exercises to get an outsider’s perspective of your security and overall compliance.

Compliance Frameworks
We develop a compliance and ethics program that is respected, owned, and lived by your business. Our team of experts can provide consulting and implementation services to help your business maintain compliance with all national and international standards.
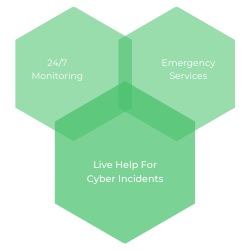
Security Operation Center (SOC)
We are certified with SOC 1, SOC 2, and SOC 3 and you can rest assured that you are secured even during non-business hours. You will be supported by subject matter experts. Monitor, prevent, detect, investigate, and respond to cyber threats 24/7. So that you will be secure no matter the time zone or occasion.
Security Operation Center (SOC)
We are certified with SOC 1, SOC 2, and SOC 3 and you can rest assured that you are secured even during non-business hours. You will be supported by subject matter experts. Monitor, prevent, detect, investigate, and respond to cyber threats 24/7. So that you will be secure no matter the time zone or occasion.

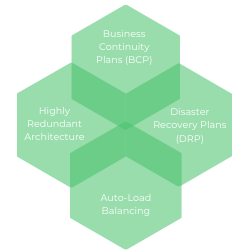
Technology Architecture & Implementation
We design & deploy architecture configurations that ensure business continuity (BCP) and disaster recovery (DRP) in the event of an attack. Our teams excel at leading your business to security by employing highly redundant architecture, auto-load balancing against DDoS attacks, and Site-to-Site recovery configurations.